installing mag lock system

Company: Store Manager & IT Specialist
Access Control & Mag Lock System Installation and Configuration
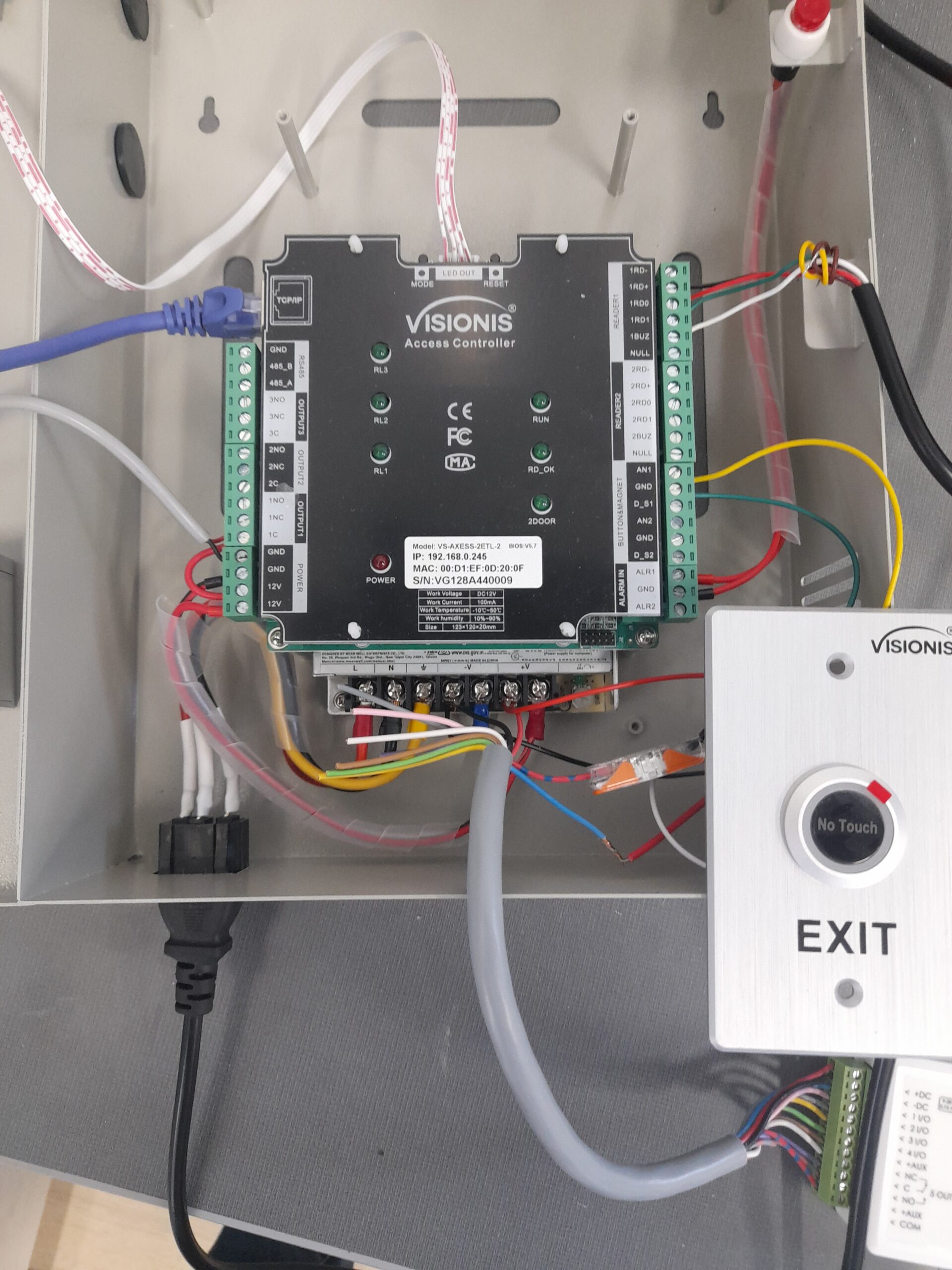
I completed a full installation and configuration of a magnetic lock access control system using the Visionis VIS-AXESS-4D-ETL (Version 2.0) networked controller. This system supports four doors, thousands of users, and detailed event logging. The project combined electrical work, networking, system configuration, and security management into one hands-on build, giving me valuable experience in both physical and digital security.Wiring & Hardware Setup
The first phase involved installing and wiring the magnetic locks. This included running low-voltage wiring from each door to the main controller cabinet, connecting power and relay terminals, installing exit devices, and verifying that the locks operated properly in fail-safe mode. I also tested alignment, engagement strength, and release timing to ensure smooth operation. This stage strengthened my skills in electrical safety, cable management, and hardware installation.Configuring the Visionis Access Control Panel
With the hardware in place, I configured the VIS-AXESS-4D-ETL controller. The system supports up to 20,000 users and 70,000 stored logs, making it suitable for auditing and role-based access management. I set up door names, grouped access points, applied permission levels, configured time-based schedules, and adjusted event log retention settings. Using the Visionis management software, I verified door activity and ensured proper communication between the controller and the network.Key Card Enrollment and User Management
I then set up employee key cards through the access control software. This involved enrolling new cards, assigning access roles, defining time restrictions, and building simple badge profiles. This process provided practical experience in managing large user databases and enforcing structured access policies.Mobile Access Integration
To enhance flexibility, I added mobile access by installing and configuring a Wi-Fi module for the system. After linking the controller with the access control mobile app, authorized users were able to unlock doors using their smartphones. This added convenience while maintaining security and proper logging.Event Logging and Monitoring
I configured detailed event logging to track door activity. This included monitoring authorized and unauthorized access attempts, verifying time-stamped records, and ensuring system alerts functioned correctly. Working with the event logs was especially useful as it reinforced my skills in log analysis—an important part of SOC and cybersecurity work.Key Takeaways
This project strengthened my capabilities in: Low-voltage wiring and hardware installation Network-based access control systems Software configuration and security auditing Role and permission management Integrating physical and digital security Troubleshooting mixed hardware and software environments Completing this installation gave me hands-on exposure to real-world security systems and helped me deepen my understanding of how physical and digital security work together. It was an excellent project that aligns closely with my growing path toward cybersecurity and SOC operations.